Cyber 201: What is Cyber Threat Intelligence?

When aspiring cybersecurity professionals consider specialties, cyber threat intelligence (CTI) often peaks their interest. Cyber threat intelligence certainly sounds cool. After all, we’ve all seen plenty of movies about spies and intelligence analysts. Most people don’t actually know much about CTI beyond its perceived desirability. It may be one of the harder cybersecurity specialties to get into. So let’s take a look at what CTI is and the skills it requires.
Newest Intelligence Discipline
Intelligence has a long and storied history. In the modern era it’s been divided into a number of intelligence collection disciplines or INTs, including:
Human intelligence (HUMINT) - gathered from a person
Signals intelligence (SIGINT) - gathered from interception of electronic transmissions
Geospatial intelligence (GEOINT) - gathered from satellite and aerial photography
Measurement and signature intelligence (MASINT) - gathered from an array of signatures (distinctive characteristics)
Open-source intelligence (OSINT) - gathered from open sources
Technical intelligence (TECHINT) - gathered from analysis of weapons and equipment
Financial intelligence (FININT) - gathered from analysis of monetary transactions
Cyber threat intelligence—sometimes called Cyber intelligence (CYBINT) in the Intelligence Community (IC)—is simply the newest kid on the intel block.
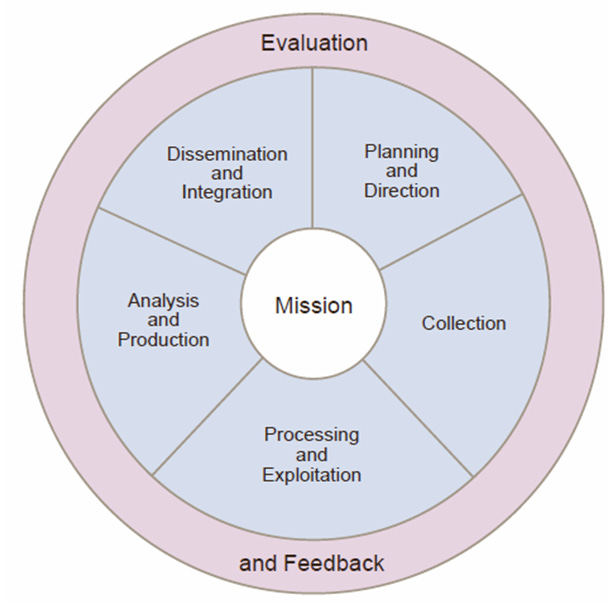
CTI still draws upon a rich tradition and methods of intelligence gathering and assessment. For example, CTI’s analytical process will look familiar to any intelligence professional. It uses the same Intelligence Cycle, which is the basis for every intel discipline.
Intel in the Private Sector
Intelligence has long been the domain of nation-states. Countries with large budgets and government mandates conducted intelligence operations on behalf of their citizens. They did so predominantly against other nation-states. With CTI the game changes a bit. Globally the majority of information systems are owned by private organizations and individuals.
Cyber threat intelligence… is simply the newest kid on the intel block.
Governments have little, if any, visibility into activity on private information systems within their country’s borders. That visibility is the domain of the private sector. This puts responsibility for CTI in the hands of private organizations. However, they lack the collection assets that governments have. Instead companies utilize a range of security vendors for collection. These vendors also help protect companies from legal liability. Depending on the industry, companies may also participate in intelligence sharing organizations, like sector-based ISACs.
Just like with countries, bigger companies with large budgets are likely to have more robust CTI programs. Smaller companies may have just one or two cybersecurity (or IT) analysts monitoring threat feeds as an additional duty. Large companies with mature CTI programs may have a fully-staffed organization of intelligence professionals, supporting a mature Security Operations Center (SOC).
Intelligence Training
Cyber threat intelligence can be a highly desired specialty for aspiring cybersecurity professionals. That’s understandable. It sounds interesting and people tend to be familiar with the concept of intelligence. A challenge is that government—military and civilian agencies—has long been the training ground for intelligence professionals.
How do you get into CTI if you don’t have neither cybersecurity nor intelligence experience? For starters you need to have a solid understanding of the technology and tools, particularly from the threat actor’s perspective. Studying for penetration tester certifications, such as the Certified Ethical Hacker (CEH), can help with that.
Just like with countries, bigger companies with large budgets are likely to have more robust CTI programs.
When it comes to CTI specifically, the cybersecurity training ecosystem is a bit less mature. There aren’t as many training courses and certifications for CTI as other cybersecurity specialties. Here are a few courses and certifications, which can help you learn about CTI and potentially get the attention of CTI recruiters and hiring managers.
MITRE ATT&CK Defender (MAD) ATT&CK Cyber Threat Intelligence | Cybrary
MITRE ATT&CK Defender (MAD) ATT&CK Cyber Threat Intelligence Certification | MITRE Engenuity
Of course, there’s always something to be said for self-education. Here are some well curated reading lists for anyone seeking to specialize in cyber threat intelligence.
CTI is growing in popularity and many organizations are seeking to grow their intel teams. If you don’t have cybersecurity or intelligence experience, it will take some work and/or time to get into CTI. That’s to be expected though. If you want it bad enough, you’ll put in the work.